Guides and Intro
Guidance and introductionary articles
I Love Xbase++ (ILX)
The portal for Xbase++ developers worldwide
You often read "ISAM" in newsletters and other communications from Alaska Software. And many people have heard it or know it from the inside out, but someonly have a vague idea of what it means. If you belong to this group, then it's worth reading this short article.
The good news first: if you...
Prolog
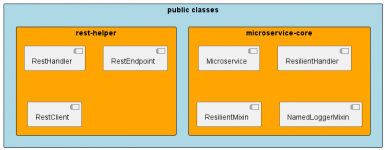
Using many small services, known as microservices, is a popular way to build applications. But, working with microservices can be very complicated. However, the complexity arises not from the Xbase++ business logic code - a domain in which an Xbase++ developer is highly proficient - but...
Background
Microservices architectures consist of loosely coupled, reusable, and specialized components that often operate independently. Microservices also use a high degree of cohesion, also known as bounded context. Bounded context refers to the relationship between a component and its data...
Introduction
Xbase++ is a development tool that offers Xbase Parts for building Windows Desktop applications. One feature that Xbase++ programmers can leverage is the ability to configure these Xbase Parts through subclassing. Not only does this approach allow for personalized coloring and UI...
Background
In the realm of software development, keeping a software product current, reliable, and robust requires a strategic approach. Alaska Software, the vendor of the programming language and development platform Xbase++, has adopted a strategy known as Continuous Delivery to maintain the...
Introduction
Composition and inheritance are two major concepts in object-oriented programming (OOP) that allow for creating complex types.
Inheritance is a mechanism where you can derive a class from another class for a hierarchy of classes that share a set of variables and methods. The...
Prolog
In the realm of software development, it's imperative for companies to adopt versioning strategies that are both meaningful to developers and aligned with modern development methodologies. Alaska Software, as the vendor of the Xbase++ platform, has seamlessly integrated these...
Introduction
Interfaces in Object-Oriented Programming (OOP) play a critical role in designing robust software. In the following we will try to explain the benefits of using interfaces and how to implement them in Xbase++. Generally, benefits of using interface are:
Abstraction: Interfaces...
In this article we will have a deeper look into how to implement different types of REST APIs using Xbase++ 2.0. We assume that a user management REST API exposes two endpoints.:
1. "POST /users" - This creates a new user. For this request, we need to send user data in the request body. The API...
Overview
In this article it is shown how the class AesCrypt() can be specialized to implement some padding schemes for encrypting and decrypting messages.
Background
The Advanced Encryption Standard (AES) standard is a block cipher algorithm that only allows for the encryption of messages in the...
Positioning
If a Smtp or Pop3 endpoint for e-mail exchange requests authorization via the OAuth 2.0 protocol, then this flow-based protocol must be used when communicating with the server to authenticating the client. This may also require displaying a user interface for obtaining the user's...
Introduction
Email providers such as Google GMail allow authentication of the Smtp and Pop3 client via the OAuth2 security protocol. Furthermore, it is foreseeable that sooner or later other authentications will no longer be allowed. Google has already announced this step.
The OAuth2 security...
Introduction
This article assumes knowledge of how to use the Asset Manager of the Xbase++ Workbench. You will find an introduction to the Asset Manager of the Xbase++ Workbench in the article Xbase++ Workbench Asset Management.
The Xbase++ OAuth2 asset implements the protocols for the OAuth2...
Introduction
Xbase++ comes with so-called assets. You can consider an asset as a reference implementation. The idea of assets is to formalize the packaging of libraries, frameworks, etc. beyond the Xbase++ core product featureset. In practice, assets are there to clean up the project chaos and...
Some technical background
When an application is loaded, the operating system's image loader examines the import directory of the exe file. In this import directory the dll names with their functions (so-called procedure entry points) are listed, which are needed for the application. These...
Background
When a source file ( .prg or .arc) is compiled, then an intermediate file ( .obj or .res ) is created that is finally linked to an executable ( .exe ) or library ( .dll ). The Xbase++ compilers xpp.exe and arc.exe create the intermediates next to their source files. This behavior is...
By default the Xbase++ WebHandler does negotiate the content type encoding automatically. The following simple AddressService returns a Object and leaves the content negotiation up to the WebHandler and the request sending party. The great benefit of that approach is that your service interfaces...